2.3. Watch out for speeding fine e-mails!¶
Received an interesting Mail this afternoon:
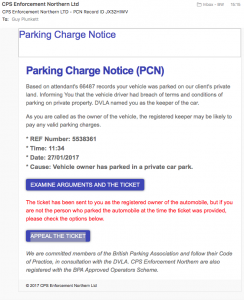
A Parking fine! really.. hmm..How did they associate my car with my e-mail address? note the contents of the mail, nothing actually identifies me.
Both the buttons link to this URL:
HXXP://gardinalli.com/wp-content/plugins/r6dmbfpitaq/mwjfuskc.php
So a word press website with some random path and PHP script at the end. Turns out this URL redirects over to here:
HXXP://jbv6.cpsnorthernonline.com/local/CPS_Enforcement/options/parking_ticket.php

Well now that’s more interesting… cpsnorthenoneline.com, was only registered on the 29th.
Domain Name: cpsnorthernonline.com
Registry Domain ID: 2093884399_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com/
Updated Date: 2017-01-29
Creation Date: 2017-01-29
Registrar Registration Expiration Date: 2018-01-29
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Registrar Abuse Contact Email: abuse@namesilo.com
Registrar Abuse Contact Phone: +1.4805240066
Status: clientUpdateProhibited
Status: clientRenewProhibited
Status: clientDeleteProhibited
Status: clientTransferProhibited
Registry Registrant ID:
Registrant Name: Domain Administrator
Registrant Organization: See PrivacyGuardian.org
Registrant Street: 1928 E. Highland Ave. Ste F104 PMB# 255
Registrant City: Phoenix
Registrant State/Province: AZ
Registrant Postal Code: 85016
Registrant Country: US
Registrant Phone: +1.3478717726
In Phoenix USA. I doubt very much the UK Parking services are using a US site. A little digging around and I find that all the sites links point to the legitimate CPS enforcement site:
HXXP://cpsnorthen.co.uk

It would seem these people have simply cloned the webpage, and then added a little capture to give value to the site. When you enter the capture your given a ZIP download.
Extract the ZIP and you get a .js file called “Ticket_information_113890.js”, currently this file is only loosely identified as malware on virus total.
All of this can easily be done using Kali linux and the social engineering tool kit!
Please everyone check your mail, and link before clicking on them. This really isn’t sophisticated but it will likely catch a few people out!
